Alright folks, let’s talk about something really annoying and frankly, quite dangerous: invoice fraud. Specifically, those sneaky fake supplier requests that pop up. I’ve seen my share of these and trust me, they are getting smarter. I figured I’d walk you through how I started spotting these rotten apples in my own processes.
It all started a few months back. We got this email that looked totally legit. It claimed to be from one of our long-term hardware suppliers, you know, the guys we order network switches and stuff from every quarter. The email said they were updating their bank details and asked us to use the new account for the upcoming payment. Sounded reasonable, right?
The Initial Alarm Bells Ringing
I almost just forwarded it to accounting, but something felt sticky. Not the email itself, it looked professional, correct logo and everything. But our relationship with this supplier goes way back. We usually get these kinds of changes via an official letter or a phone call confirming things—not just a plain email. That was my first red flag.
- Unusual Communication Method: A big change like bank details should come through established, secure channels. Email felt too casual for such a critical update.
- Sense of Urgency: The email used phrases like “immediate attention required” because the “old account is closing soon.” Classic scare tactic.
I decided to stop and dig deeper. I didn’t just reply to the email—that’s what they want you to do. I pulled up the actual contact information we had for our supplier from our internal records, the one we used for years.
My Verification Process: Double Checking Everything
I skipped the email thread entirely. I picked up the phone and called our usual contact, Sarah, at the supplier’s office. I didn’t even mention the email yet. I just asked her if everything was okay with their accounts for our next purchase order. She was confused.
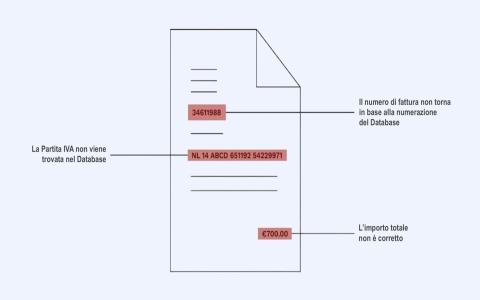
BAM! She confirmed they had made absolutely no changes to their banking information. That’s when I knew we had been targeted. I then forwarded the suspicious email to Sarah, and she confirmed it was 100% fake. The domain name was slightly off, too, when you looked closely at the header—like “*” instead of “*.” That tiny hyphen was a killer.
After that close call, I standardized a few checks for any vendor requesting a change to payment details, no matter how small or big the supplier is. You just can’t trust paper or pixels alone anymore.
Setting Up New Guardrails
I documented this whole mess for the team and put a mandatory three-step verification process in place for any financial changes:
- Cross-Reference Email Details: Always check the sender’s actual email address, not just the display name. Look for tiny errors, extra characters, or different extensions.
- Mandatory Voice Verification: We now mandate a phone call to a known, established contact number (pulled from our ERP system, not from the suspicious email) to confirm any change in bank details. We actually read the new account number back to them to ensure accuracy.
- Internal Paper Trail Requirement: The request must be accompanied by an official, signed document from the vendor, which we then scan and file. No document, no change. Simple as that.
The key here is don’t take the easy road. If an email asking for money feels too pressing or slightly out of character for that vendor, stop. Just pause, breathe, and grab that phone number you know is real. Fakers rely on speed and folks being too busy to check. We started slow, put these steps in place, and haven’t had a successful fraud attempt since. It’s a pain, but better than losing thousands of dollars.